Gamers risk getting played by Hackers
Let's play - the rise of online gaming accounts
If you’re in your mid-twenties or beyond, you will be familiar with people at family gatherings saying ‘remember when we didn’t have all these gadgets, and we used to actually talk to each other?’ The answer to this is ‘no’ – the level of conversation has remained largely unchanged, it’s just now we have gadgets and gizmos to occupy our attention during these moments of strained silence.
Personal gripes aside, there’s no denying that we all spend a lot more time staring at a screen than in the past, and increasingly this is down to gaming. Children especially spend many hours transfixed by games as they play through the latest releases and trending downloads. Increasingly, games are focussed on multiplayer, requiring online accounts and the option to buy digital assets with real money, resulting in player communities with their own economy and ecosystem. You might not think that the video game industry is of much interest to us cyber security types, but what if I told you that the infamous Mirai botnet was created by Minecraft enthusiasts in order to take down rival servers? And what if I told you that a recent report showed that out of 55 billion cyber attacks, 12 billion targeted the gaming industry?
The start of in game hacking
When one thinks of online gaming, for us uninitiated, the mind immediately goes towards MMORPGS, such as World of Warcraft. With a sizable and loyal player base, it wasn’t uncommon to see people selling their hard earned in-game currency for some of that slightly more useful real currency. Human nature being what it is, people reasoned that it would be quicker and easier to steal someone else’s hard-earned in-game currency than acquire it legitimately themselves. And thus, game account hacking was born.
Through credential stuffing, brute-forcing or just taking advantage of accounts listed in previous breaches, cyber criminals can take over accounts and sell off the digital assets to whomsoever wishes to purchase them. This is a problem that’s still alive today and is earning hackers a small fortune on games like Fortnite. Whilst this may seem like fairly ‘low-level’ criminality, it is still theft, and can quickly add up to thousands of pounds per week. And if you want something a little juicier, it’s been said that some in-game currencies are used for laundering purposes.


Player 'Cyber Criminal' has entered the game
The more popular an online game is, the more targets a hacker has and the more likely it is that someone somewhere will fall for their trickery. Returning to Fortnite, overly competitive players looking for a way to gain the edge over their opponents naturally started looking for cheats. Cheats hackers will happily provide – or so it would seem. A supposed hack dubbed ‘aimbot’ promised to provide players with better aim assist, because games are more fun when you don’t have to play them yourself. Unfortunately, this hack did not do what it said on the tin and was instead our old friend ransomware. This is just one of many scams and general cyber shenanigans relating to this popular game. Some estimate Fortnite scams have hit the 53,000 mark.
Digital marketplaces are also a target
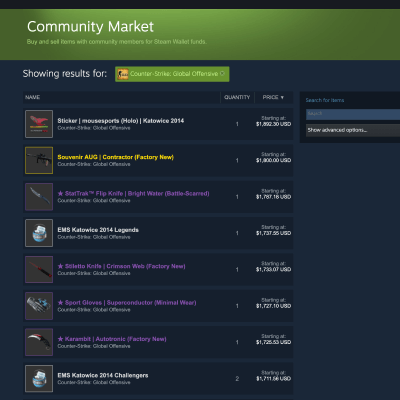
Believe it or not, if previous generations wanted to enjoy some content, be it some music, a good book or a video game, they had to use their legs to carry themselves to a purveyor of such goods. It sounds positively barbaric by today’s standards, where digital marketplaces reign supreme. The most popular of these digital marketplaces is Valve’s Steam.
The platform makes billions every year, with independent developers showcasing their wares alongside the big players, and it boasts a huge dedicated community. Interestingly, it took an independent bug hunter to reveal a bug that could have handed hackers control of people’s computers. From here, they could get credit card info and other personal data or launch further attacks, such as ransomware. There’s a similar story in gaming giant EA’s Origin marketplace.
These particular flaws have since been fixed, but it’s worth noting the platforms were live and vulnerable for a long time, and there’s no telling what other bugs might be lurking in any platform. The next issues might not get picked up by an ethical hacker. Or they might be, but the companies may choose to be less than grateful. Hell hath no fury like a bug bounty hunter scorned.
In these sorts of marketplaces, users usually have their card details linked to their accounts. Whilst this information should be encrypted, it’s not beyond the realm of plausibility that hackers might be able to use a compromised account to make purchases. Vulnerabilities could be lurking anywhere, which is why these platforms tend to need regular penetration tests.

Malware and malicious links
Taking a broader view of the industry, playing online games with people may give you the false impression that you know them. If you’ve just finished a great game with AstroMax92 and they send you a private message later saying ‘that was great. Want to join my clan? Here’s a link for more info,’ you might not think twice about clicking said link. Not thinking twice about clicking a link, it’s fair to say, is a very common cause of getting hacked. Links can be left behind on any forum by supposedly helpful strangers. For the most part they’re fine, but as always, it just takes one rapscallion to ruin it for the rest of us.
It's a similar story with modding: which is a popular way of adding extra content or elements to an already existing game, such as replacing dragons with Thomas the Tank Engine. It’s also a clever way to get malware onto people’s machines. In the early days, these exciting additions or changes were found scouring the internet and finding an executable before downloading and installing it. This was one sure fire-way to get your PC riddled with malware.
These days, modding communities tend to be well regulated and user feedback means that mods concealing malware don’t last long, but that’s of little solace when you’re one of the unlucky few whose processor is melted by cryptomining malware.
Mobile gaming risks
Increasingly powerful smartphones allowed for a new era of handheld gaming where the only limit was the human imagination. There’s Candy Crush, where you must match three or more of a kind. Bejewelled, in which you must match three or more of a kind. Then there’s The Bubble Witch Saga, that sees you frantically matching three or more of a kind. The possibilities are endless.
In the last half a decade or so, mobile games have exploded in popularity – a trend that looks set to continue. Many of these apps generate revenue through showing ads between rounds. You’ll find certain apps, particularly on the Android store, take things further by installing adware. Back in 2018 a batch of malicious apps were downloaded over 500,000 times. All sorts can slip through disguised as a mobile app from adware to cryptominers and beyond. And with everything these days requiring an account, and with children increasingly a target market for gamers, there’s a lot of highly sensitive personal data floating around a lot of servers too. It’s a GDPR headache for sure.
Even if apps don’t contain malicious code, they’re not necessarily being built securely. Oversight, rushed jobs or lack of knowledge may mean some of those harmless mobile games are putting your devices or personal information at risk. Ideally, any app should be thoroughly tested by experts before they’re publicly released, but we do not live in an ideal world.
Protecting gamers from hackers
Obviously, this is not to say that the gaming industry is terrible from a cyber security perspective – a lot of companies are doing a lot of hard work in an attempt to stay secure. As with any area online, tread carefully, be careful what you sign up for and what you click on. As we’ve just demonstrated with gaming (which is an industry seen as innocuous by most), every single industry is a target for hackers. Wherever there’s money to be made, cyber criminals will appear, and gaming is a big business that’s only going to get bigger.

The bulletproof approach to cyber security
As we at Bulletproof know from our blue team SIEM operations, hackers’ strategies are constantly evolving, and their attitude to exploiting the gaming industry is no exception. Trends are slowly moving away from personal data and more emphasis is being put on monetising the theft of digital assets. There might be many reasons for this, but a big contributing factor will be the sheer level of competition when it comes to selling personal data. Whatever it is hackers go after, the fact is this billion-dollar industry will always attract them.
We know that developers, publishers and market platforms need to be booking regular penetration tests on their products to resolve any issues before they affect customers. As the industry grows, it becomes increasingly clear that we need more people using their hacking knowledge for good.
At Bulletproof, security is in our DNA. We’re dedicated security specialists, combining years of industry experience with cutting-edge technology and in-depth knowledge across all fields of information security.
If you are interested in finding out more about Bulletproof and what we do, have a browse around or contact us today. If you think you are Bulletproof material, check out our vacancies to see if we have anything for you.
10 Steps to Cyber Security
Find out how to secure your business in 10 steps with our free best practice infographic.
Download nowRelated resources
Trusted cyber security & compliance services from a certified provider
Get a quote today
If you are interested in our services, get a free, no obligation quote today by filling out the form below.








