What is penetration testing? The complete guide from Bulletproof
Modern cyber criminals can launch large-scale attacks on your IT infrastructure with unprecedented speed and intensity. Penetration testing, meaning a proactive assessment of your security through simulated and controlled cyberattacks, is a fundamental component of your defence against these evolving threats.
This comprehensive guide will help you understand what penetration testing means, how it works and why it should be a cornerstone of your risk management strategy.
Contents
What is penetration testing?
So, what is penetration testing, exactly, and how does it help to protect your organisation? The simple definition of penetration testing (or pen testing) is a controlled, technical exercise that aims to methodically test the security of your IT infrastructure and your employees.
During a pen test, a qualified penetration tester takes on the role of a hacker and uses the latest tools and technologies to identify weaknesses in your systems, applications and even human behaviours (a method called social engineering – for example, the tester may target your employees with phishing emails).
The tests or ‘attacks’ take place within a defined scope and timeframe agreed between you and the testing company.
The aim of penetration testing is twofold. Firstly, to uncover and exploit flaws in the confidentiality, integrity and availability of your information, to allow the exposure of the business risk. Secondly, to provide actionable remediation advice that will help you improve defences and reduce the impact of the risks that the tests reveal.
These are both critical steps that will help you to optimise your risk management programme.

Get a fast quote for penetration testing services
Get my fast quoteHow does penetration testing work?
Penetration testing is a critical aspect of modern cybersecurity, designed to identify and exploit vulnerabilities in systems, networks, and applications. Although its origins date back to the emergence of computer security in the 1960s, penetration testing has evolved into a structured and highly effective practice and follows a systematic methodology that combines cutting-edge tools, innovative techniques, and expert insight.
Today, all testers follow a standard methodology that includes 5 core stages of penetration testing.
-
Intelligence Gathering & Threat Modelling
In the initial information reconnaissance phase, the tester gathers as much information as possible. This information is then used as attack vectors during the subsequent vulnerability assessment and exploitation phases.
-
Vulnerability Analysis
The vulnerability analysis phase aims to discover flaws in your networks, systems, and/or applications. This is typically done using active and passive mechanisms, including identifying host and service misconfigurations, assessing current patching levels, and analyzing insecure application designs.
-
Exploitation
After the vulnerability analysis, the tester attacks all external and internal-facing systems within the project's scope. This involves using a combination of available and custom-made exploits and techniques to tamper with improper configurations, bypass security controls, access sensitive information, and establish access to agreed targets.
-
Post-Exploitation
The post-exploitation phase determines the value of the compromised targets by trying to elevate privileges and pivot to other systems and networks that are defined within the test scope. Importantly, the tester cleans the compromised systems to remove any scripts and additional attacks launched. This makes sure the systems don’t carry unnecessary risks as a consequence of their actions.
-
Reporting
Following these clearly defined stages of penetration testing the company provides you with a report. This should include:
- All risks based on the current server/application setup/configuration
- Vulnerabilities and running services for the servers and applications
- What has been done to exploit each security issue
- Recommended remediation steps
- Near-term and long-term actions
- The overall business risk exposure
-
Before the Process: Scope Definition & Pre-Engagement Interactions In this phase, we gather requirements, set goals, and agree on types of tests, forms, timelines, and limitations (such as time limits) for the project. This is essential for a smooth and well-controlled exercise.
-
After the Process: Customer De-Brief When we’ve completed the penetration test, we provide a de-brief session to explain the findings and risks listed in the report and give you the opportunity to ask questions. This step isn’t a strict requirement, but it is good practice that can significantly enhance your understanding of the results and our recommendations.
Potential vulnerabilities that couldn’t be exploited during the test are also included in the final report.
In addition to the five core stages of penetration testing outlined above, there are two supporting phases that are crucial to the success of any penetration testing engagement. These phases ensure that the testing is both effective and actionable.
Automated vs Manual penetration testing
Finally, it’s important to understand that there is a difference between automated and manual penetration testing. Automated testing refers to vulnerability scanning of your systems and applications using automated tools. Manual penetration testing is where penetration testers use the latest tools to try and exploit your vulnerabilities. While automated testing is typically less expensive, manual penetration testing is the more effective because it provides deeper and more comprehensive analysis.
The benefits of penetration testing
Research from IBM global average cost of a data breach is now $4.88m the global average cost of a data breach is now $4.88m, the highest total ever. Against this backdrop, penetration testing has many advantages for organisations that want to protect themselves and avoid significant disruption and costs.
-
Stay One Step Ahead of the Hackers
One of the main, overriding benefits of penetration testing is that it will test your current security posture and provide a clear indication on where you stand against the ever-changing threat landscape. In short: it’s how you identify and address vulnerabilities before an attacker does.
-
Take Control of Your Infrastructure
Technical infrastructures become increasingly complex as your technology evolves and your organisation grows. Your oversight of this complexity can easily slip out of control, or you might not have the relevant expertise to ensure that you’ve implemented controls the right way. Each penetration test reveals the flow of your environment and any interdependencies that have a direct or indirect impact on security.
-
Prove Your Security Credentials
Penetration tests provide up-to-date assessments of your security posture which are important for meeting compliance standards such as PCI DSS and ISO 27001. Compliance with these standards will help you to demonstrate your commitment to information security to customers. It will also help you streamline your sales process by reducing the work involved in responding to extensive security documentation requests.
-
Manage Risk
Each penetration test addresses your business risks and the impact of those risks on the confidentiality, integrity, and availability of your data. This helps your management and technical teams better understand how to prioritise, plan, budget, and remediate the risks in a structured manner.
-
Keep Training Up to Date
One of the other major benefits of penetration testing is that it often highlights lack of training in critical areas of IT and development, such as poor knowledge in hardening, secure configuration, and development best practices. This is useful insight to have: it will help you to bake-in security at the most foundational parts of your infrastructure.
-
Protect Your Business
Security breaches can severely impact your brand’s reputation and the financial stability of your organisation. In this context, the advantages of penetration testing are clear. It helps you drastically reduce the risk of a breach so you can better protect your organisation and retain the confidence of your existing and potential customers.
Get a fast quote for penetration testing services
Get my fast quoteTypes of penetration testing
Pen testing is designed to stress test every aspect of your organisation’s defences. This means there are several different types of penetration testing, with varying objectives, depth and duration. The tests your business needs will depend on your requirements and selected approach. Here are some examples of the most common types of penetration test that can help to reveal vulnerabilities:
Cloud penetration testing
Cloud penetration testing is specifically designed to expose insecure functionality and misconfigurations in the cloud. Common vulnerabilities that tests reveal include Identity Access Management, lack of Multi Factor Authentication and insecure APIs. Penetration testing cloud technology is vital for securing the cloud-based infrastructure, applications and data that many organisations now rely on.
Mobile application penetration testing
Mobile application penetration testing uncovers and exploits security vulnerabilities or misconfigurations in apps built for Android and iOS. Ideally, organisations should integrate mobile application penetration testing into the software development lifecycle to ensure a safer experience for the end user. The tests can also help to identify issues with old versions of apps that can persist on end user devices for years, posing potential risks even after updates.
Web application pen testing
Web application pen testing evaluates the features, functions, and technical security of web apps. Common vulnerabilities such as SQL injection and cross-site scripting are identified and exploited to assess risk. This is important: web apps are often vulnerable because of security flaws that have been present since the earliest stages of their development, therefor integrating penetration testing into the software development lifecycle is crucial. This ensures vulnerabilities are identified and mitigated throughout the app’s development and deployment phases.
API penetration testing
Closely related to web application pen testing, API penetration testing focuses on identifying vulnerabilities in application programming interfaces (APIs) that your web apps rely on. APIs are critical components in modern web applications, making them a frequent target for attackers.
Integrating penetration testing into the software development lifecycle ensures that APIs are tested alongside web apps, allowing vulnerabilities to be identified and addressed consistently throughout the development process. This is essential to maintaining robust security across your entire application ecosystem.
Infrastructure or Network penetration testing
Network pen testing, sometimes called infrastructure pen testing, assesses your infrastructure or your network for its current operational security levels, such as running services, current patch levels, improper configurations, flaws in design and effectiveness of security controls. The goal is to identify and exploit any associated vulnerabilities.
Red team security testing
Red team security testing is an adversarial, threat-led method of security testing. A highly skilled pen test team will aim to breach your defences by employing real-world tactics to simulate an attack by a persistent threat actor targeting your cyber defences and testing the responsiveness of your security team.
Red team security testing is an objective-driven method of security assessment, where the testing simulates the approach of a determined adversary working toward a specific goal. The goal of the engagement is to achieve a defined objective—such as accessing sensitive data, bypassing physical security, or compromising critical systems—by exploring the paths a real-world threat actor might take to achieve their aims. This includes testing networks, systems, physical security, and people to evaluate how an organisation would fare against a targeted attack.
Social engineering testing
Social engineering testing investigates your non-technical ‘human’ security defences. The most common form of social engineering attack is email phishing, where hackers attempt to trick your users into granting permissions, giving credentials, visiting malicious links.
By conducting social engineering testing, you can understand where your non-technical security weaknesses are and how to improve them – for example, through more regular and relevant security training.
Wireless penetration testing
Wireless pen testing is designed to uncover vulnerabilities, exploit network security flaws and expose insecure functionality in your wireless systems. During a wireless penetration test, the pen tester will seek to identify weaknesses by analysing and inspecting packets, access points, rogue devices, encryption features and patching levels.
Penetration testing methodology
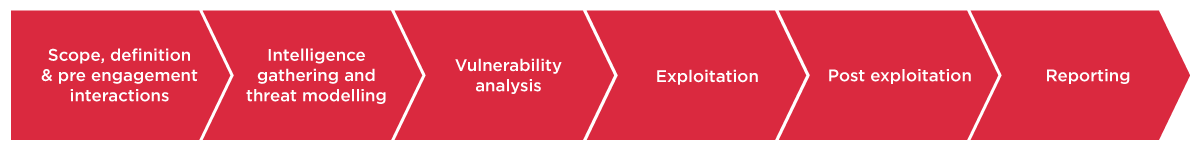
As we’ve already explained, most companies follow a standard methodology for penetration testing that has five stages:
- Intelligence gathering & threat modelling
- Vulnerability analysis
- Exploitation
- Post-exploitation
- Reporting
These stages are guided by widely recognised methodologies such as OWASP and PTES standards and methodologies for penetration testing, both of which we follow at Bulletproof. However, there are other methodologies that may be followed depending on the context, type, and approach of the penetration test.
Get a fast quote for penetration testing services
Get my fast quoteBlack, white and grey box tests
Penetration testing methodology also includes black, white and grey box tests.
The type of box test your pen tester deploys will depend on what the customer wants to achieve and how to simulate the assessment. This will also determine the levels of detail the test reveals about your organisation and its security posture.
- Black box penetration test: In the black box testing scenario, the penetration tester has no prior knowledge of your IT systems or any login credentials. This means the testing environment simulates a real-world cyberattack. The black box pen testing methodology is designed to show how hackers could target your organisation without user access privileges. However, because you don’t disclose any information before the start of the test, various components may remain untested.
- White box penetration test: A white box test provides the tester with full visibility and access to the internal systems and environment being tested. This approach allows for in-depth internal testing at all access levels, making it useful for uncovering vulnerabilities that might otherwise remain hidden. However, it is considered the least realistic scenario, as it works from an inside-out perspective—a situation unlikely to mimic real-world external attacks. Despite this, white box testing is valuable for comprehensive security assessments where detailed insights into internal system weaknesses are needed.
- Grey box penetration test: Grey box testing uses a hybrid approach between white box and black box penetration testing methodologies. In this scenario, pen testers are provided with limited knowledge or access to the target, simulating a situation where the attacker has partial, legitimate access (e.g., as a registered user of an e-commerce platform). This approach allows testers to identify vulnerabilities that could be exploited by someone with restricted but valid access, such as an insider, a compromised user account, or a customer. Grey box testing is valuable because it provides a balance between real-world conditions and deeper insight into the system’s potential weaknesses.
Positioning of penetration tests
In addition, penetration testing methodology includes decision making on whether tests need to be positioned and executed externally, internally or from both angles. Internal & external network penetration testing is crucial for identifying vulnerabilities across your entire infrastructure, ensuring security from both outside threats and potential insider risks. The target is the same: the difference is from where the attack will originate.
- External-based penetration testing simulates the ability of an attacker to gain access from external resources to the internal network or to retrieve sensitive data from public-facing resources, such as web applications or email servers.
- Internal-based penetration testing simulates an attack where the hacker has already bypassed the security perimeter. This addresses what an attacker (or an insider) can see and what they can do internally, such as moving from one network to another or intercepting internal communications.
Penetration testing tools
Underpinning these methodologies, there are several specific penetration testing tools (or pen testing tools) that testers use to gather insight on your security posture and provide you with actionable insights.
These pen test tools include:
-
Open and closed source intelligence
Open Source Intelligence (or OSINT) gathers publicly available information about the target from open sources such as the internet and social media. Closed Source Intelligence (or CSINT) involves collecting non-public or restricted information often acquired through authorised access or insider channels. When combined, OSINT and CSINT provide a rounded approach to penetration testing that allows testers to simulate the attack vectors of both an external attacker and an internal threat.
-
Enumeration tools
Enumeration tools help to identify and interact with services, protocols, and applications to gather deeper insights about their configuration. The goal of these pen test tools is to identify and map out potential attack surfaces and provide the tester with the information they need to launch an attack on your organisation.
-
Web proxies (forward and reverse)
A proxy server (or forward proxy) is a server application that acts as an intermediary to separate end users from a website to protect their privacy or block unknown traffic. A reverse proxy works the other way and is designed to protect servers. Penetration testers use these proxies as a tool to intercept, modify, and analyse different types of traffic to detect vulnerabilities that may enable an attack.
-
Vulnerability scanners
A vulnerability scanner is penetration testing software that identifies known vulnerabilities in your applications, infrastructure, and cloud environments, such as missing patches, weak passwords, or other security risks. Although testers usually perform vulnerability scans with specialised software, they can also choose to perform the scan manually.
-
Exploitation and post-exploitation frameworks
Exploitation frameworks help testers take advantage of vulnerabilities discovered during the reconnaissance and scanning phases of penetration testing. Post-exploitation frameworks help testers to continue their analysis after they have gained access to the target system, enabling them to explore other systems in the network through lateral movement, compromise components, and manage persistence (i.e., maintain access). These penetration testing tools are valuable when they work in tandem to simulate persistent and invasive real-world attacks.
-
Emulators and dedicated environments
Emulators are pen testing tools that safely test exploits, analyse vulnerabilities, and simulate attacks in a virtualised environment. Dedicated environments are isolated setups of hardware and software that are separate from the rest of the network. Penetration testers use both these tools to conduct tests without compromising live production systems.
-
Custom scripts
Custom scripts are tools that testers create to introduce further flexibility and adaptability into the process. For example, custom scripts allow penetration testers to exploit specific vulnerabilities in environments where standard tools may not work. They can also use them to automate actions such as enumeration.
Penetration testing cost
As you will probably have realised from reading this article, there is no simple answer to the question of what penetration testing costs. Penetration testing projects vary in length and complexity depending on a number of factors, including what apps and infrastructure you want tested, the aims of the test and the testing parameters. The cost of penetration testing therefore varies according to these factors
As a leading UK penetration testing service provider, we take the time to understand your aims and objectives, so we can scope a best-fit security test that delivers value for money. As a specialist penetration testing company, we have dedicated pen test scoping experts to help you get the best outcome for your pen test.
Why choose Bulletproof for penetration testing?
We hope you’ve found this information for understanding what penetration testing is, how it works and the value it will deliver for your organisation.
At Bulletproof we bring innovation and simplicity to all areas of cyber security, data protection and compliance. As part of our service, we offer comprehensive manual and automated penetration testing and have become a leading global pen testing company.
Our customers choose us over other pen testing firms because we offer:
Continuous security protection - protect your business 24/7 with automated scans included with every penetration test.
Competitive pen test prices – our prices are highly competitive compared to other pen testing companies but without sacrificing quality.
CREST Certified Security Experts – our pen test teams are qualified by industry recognised certification bodies, including CREST.
A modern dashboard driven platform - our simple to use dashboard prioritises test results and gives you key remediation guidance.
What our customers say
Find out how our penetration testing service provided Traced with clear, actionable advice that enabled the business to improve its security posture and meet a critical go-to-market deadline.
Get a fast penetration test quote
Stay ahead of the hackers with penetration testing services to protect your systems, networks, apps & more.
- One of the leading pen test providers in the UK
- Combines automated scanning & human expertise
- Detailed threat analysis & breakdown
- Remediation advice with each threat
- Track threats & manage remediations
- Get a big-picture view of your security
Find out more
For more information on this topic download our whitepaper
Security First: An Essential Guide to Penetration Testing