Phishing awareness & prevention
Phishing is just as dangerous as it’s ever been. Why not beat the hackers and phish yourself? Discover how to do exactly that with our help.

Introduction
We are all no doubt aware of phishing. That age-old practice of sending fraudulent emails with the hope of gaining financial details, obtaining account credentials or tricking a user into installing malicious software. The practice is not new. In fact, before the wide-spread use of the internet, people would often receive letters claiming that they had won some sort of competition and to claim their prize, all they had to do was send some cash to front the delivery costs. I believe that many cave paintings are in fact prehistoric phishing campaigns stating that in order to obtain a free mammoth, all one had to do was leave some shiny pebbles outside their cave at night.
Share this Article
Surely then, we should have all cottoned onto the tricks employed by these mischievous beings. Especially when it’s common for a phishing email to look like this:
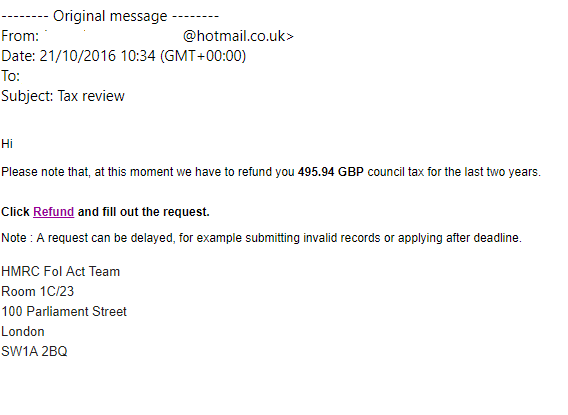
Now, there are several subtle signs that this email is not genuine. Those of you in the know will immediately realise that the HMRC is not responsible for council tax payments. More to the point, even in this age of austerity, it’s extremely unlikely that the HRMC are going to opt for Hotmail accounts.
Why is phishing common?
However, the fact is, phishing only continues to exist because it works. Very few people will take the time to draft and send out these sorts of messages just for the fun of it. As it stands, phishing (and other kinds of social engineering) is often the easiest way to gain access to and compromise a network. No matter how good your cyber security is in terms of tech and processes, you’ll never get rid of the weakness between the keyboard and the chair.
“But, no one I work with would be foolish enough to fall for that,” I hear you cry. Firstly, that’s probably not true, as to quote Voltaire, “common sense is not so common.” Secondly, I deliberately chose that light-hearted example because I was feeling whimsical, but now it’s time to get serious.
The risks of social engineering
In the hands of someone who really knows what they’re doing, the phishing email can be devastating to a business. It is the #1 method for sneaking ransomware into a company’s network.
A well-crafted phishing campaign can be quite sophisticated, going far beyond the blanket approach. Someone who knows what they are doing will really go the extra mile to make their malicious email look legitimate. In this respect, spelling and grammar is key. Awkward phrasing and frequent spelling errors are an instant giveaway. As in all cases, a lot comes down to appearances. Another key aspect to a successful phishing email is research.
Targeted phishing
Spelling, grammar and now research. It all sounds very much like being back at school, only with fewer fart jokes. There is a lot of information floating around on public sources that hackers collect and add to their box of phishing tackle. Your company website could well be freely giving information away. For example, many sites will have an ‘about us’ section (or more frequently a ‘meet the team’ section), which lists a number of key personnel and their position within the company, maybe even with their email address. And if your website doesn’t, then Linkedin probably does.
For example, a site might feature the smiling face of Dave Smythe, Head of IT and Infrastructure, along with a contact email. If not, the hacker now knows that Dave Smythe is the Head of IT and Infrastructure, and then can seek out details from other sources.
Armed with this email, they can craft a targeted message that appears legitimate and resembles the sort of email poor old Dave receives on a daily basis. With an incredibly busy inbox and an even busier schedule, Dave might think nothing of a polite, formerly written email from a supposed technology company asking him to ‘please see attached invoice for your recent order of X’. Only, soon after opening said invoice, his computer informs him his files have been encrypted by a nasty strain of ransomware.
Spear phishing
Going a step further, armed with this email address and perhaps one (or more) others, hackers can indulge in a spot of spear phishing. Using a few tricks, a malicious party could spoof their email to make it appear as if it’s coming from Dave, who is not having a good week. Doing so would allow them to target other individuals within the company.
There are many directions a hacker could go with this. They could target someone within finance, requesting that they approve a payment for the latest IT purchase to the specified account, thereby conning the business out of money. The more likely scenario, however, would be to leverage Dave’s position to A) encourage people to install malware via a malicious attachment, or B) inform users that, due to an IT issue, they should all change their passwords. He would even give them helpful instructions on the best way to do this. Everyone trusts Dave, and he’s the head of IT, so there’s no reason not to follow his link... right?
Email scams
It doesn’t stop there. I’m sure we’ve all received a message from someone pretending to be ‘Apple’, telling us we need to login to our iTunes account on the provided link for one reason or another. Even if you don’t have an iTunes account (for me, that was the biggest give away). This is because a large percentage of people use iTunes and are used to getting regular emails relating to it. The chances are, people don’t actually read the emails in their entirety.
The right design and apparent branding may even make up for poor content. It might only take a cropped Apple logo somewhere in the body of the email to have us convinced. Those convinced by a shoddy email are not likely to question giving their credentials away.
But it’s not just a branded email that can be deceiving. It’s all about what comes after. Even in the example given at the beginning, they provided a link. Hovering over that link shows the following:
Now, anyone in a hurry wouldn’t think much of that. It looks like it could be legit right? It’s just internet nonsense. In a better email, that may have been half convincing. Surprisingly, this site only died a death in January of this year.
Behind these links are often extremely convincing web portals or login pages. Like this for example:

Believe it or not, that is not a portal for Outlook’s web app. It was in fact knocked up by one of our penetration testers here at Bulletproof (I’ve blanked out the full URL). They even went so far as to make sure it is HTTPS. It looks like Outlook and it even says ‘secure’ in the top left corner, it’s green and everything. But type in your credentials and malicious parties would have access to your network whenever they want. Or until your password expires, and you change it from Monday01 to Monday02.
So, a good phishing email will be well constructed, often branded and seemingly from a trustworthy source. It will contain a convincing attachment or links to a well-designed spoofed page. Suddenly, you have something that has the potential to get through all of your defences and do some serious damage.
We all know the golden rule ‘don’t open an attachment from someone you don’t know or weren’t expecting’, but like most rules, this is often disregarded entirely. Your business will receive phishing emails. That’s pretty much inevitable. So, why not beat the hackers to it and phish yourself?
Employee training
Conducting phishing campaigns against your organisation can have many benefits. This might sound bizarre and a bit like saying you can test your response to ransomware by installing ransomware but bear with us.
Much like a penetration test can help you find vulnerabilities and uncover weaknesses within your network or application, conducting a phishing campaign can test your vulnerability to this form of social engineering. In fact, many companies opt to have these conducted as part of their penetration testing for a more all-encompassing security report. As more and more often, it’s the threats from within you need to look out for.
You can choose to target specific departments, remote workers, executive level staff or everyone across the business. By sending a crafted message with an attachment or a link, you can use special tools to track who opened the email, who replied to it and who clicked the links or downloaded the file. This isn’t so you can name and shame (though that’s really your business), but so you can gauge whether more training or stricter policies are needed to keep your business safe. If people are going to make the mistake of engaging with a phishing email, then it’s better they make it when no harm will come of it.
If you hold a lot of financial information, or personal data belonging to customers, you need to ensure that it is all being kept as secure as possible. If members of staff are likely to compromise security, then this is going to have a huge impact to your reputation.
Bulletproof your phishing campaign
Of course, you could just get Bulletproof to conduct a phishing campaign for you. Working to a predefined scope, we can tailor a project to suit your business and even design spoof portals specific to your needs. We can track engagement and provide recommendations based on the results.
As already mentioned, it’s a good idea to include some phishing or other social engineering elements with a penetration test for a comprehensive security review. All our testers are CREST approved, and they all enjoy a bit of phishing.
In the meantime, try not to get caught out. And don’t open attachments from people you don’t know or from emails you weren’t expecting. Also, don’t accept sweeties from strangers.
Interested in adding a phishing campaign?
Dear sir/madam, you may be entitled to a tax refund. Click to learn more
Learn moreRelated resources
Trusted cyber security & compliance services from a certified provider
Get a quote today
If you are interested in our services, get a free, no obligation quote today by filling out the form below.








