Top 5 Most Common Application Vulnerabilities in the UK
>The most common application vulnerabilities will come as no surprise to cyber security experts. If we know about them, why do they persist?
Applications are complex and are often first designed to be functional and launched to a deadline. This puts pressure on developers and it's easy to introduce vulnerabilities. The complexity of applications and infrastructure continues to increase again leading to a challenge for developers to stay on top of security best practices. Introducing the right controls, tools, and processes to help developers release code quickly and securely is crucial to reduce the chance of introducing vulnerabilities. An SDLC (Software Development Life Cycle) needs to be backed with training so that it becomes part of developer's day to day work which will lead to a frictionless secure development strategy.
At Bulletproof, we deliver hundreds of penetration tests a month that identify thousands of application vulnerabilities a year. Unsurprisingly, it’s often the same vulnerabilities that occur year on year. We have taken the top five web app vulnerabilities and added in some useful tips for achieving overall prevention. As the business landscape changes, so do our ways of working, opening new attack vectors to threat actors. Prevention is better than cure.
The top 5 web application vulnerabilities in the UK
| Vulnerability | % of total | |
|---|---|---|
| 1 | Broken Access Control | 7.11% |
| 2 | Stored Cross-Site Scripting (XSS) | 6.09% |
| 3 | Vulnerable and Outdated Components | 4.06% |
| 4 | Cross-Site Request Forgery | 3.05% |
| 5 | SSL Misconfiguration | 2.79% |
A worrying 60% of all web app vulnerabilities in the UK are classified as critical or high risk. Even more shockingly, the likelihood of these being exploited is 1 in 3. These numbers are hard to ignore and when you factor in the ease of resolving these business-critical issues, it seems logical to ensure the proper measures are in place to safeguard your business.
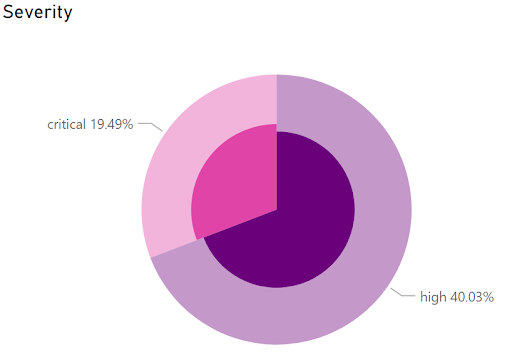
A concerning high number of critical issues in the UK.
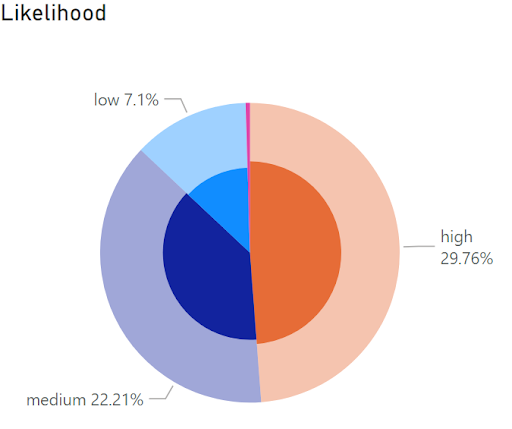
Overly high likelihood of exploitation of these UK critical issues.
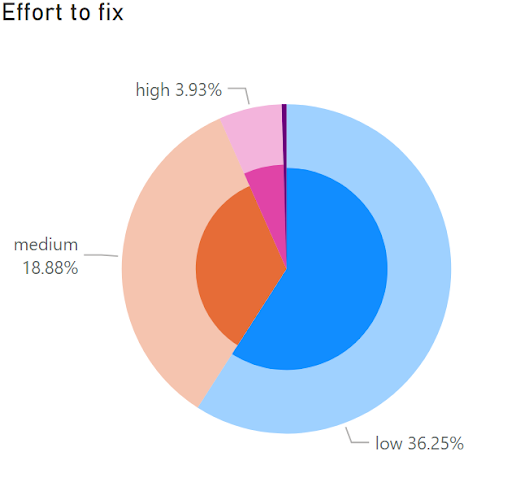
Low effort to fix is still high.
Web application vulnerabilities in the UK data
For now, we’re going to focus on web application vulnerabilities. With more than 1.6 billion websites, they hold an inconceivable amount of sensitive information and are at significant risk to cyber attacks. The ubiquity of web applications makes them attractive to cyber criminals and also the most common target. Many of these vulnerabilities feature in the latest OWASP Top Ten or have in the past.
| Vulnerability | % of total | |
|---|---|---|
| 1 | Stored Cross-Site Scripting (XSS) | 11.92% |
| 2 | Broken Access Control | 10.88% |
| 3 | Vulnerable and Outdated Components | 7.25% |
| 4 | Cross-Site Request Forgery | 6.22% |
| 5 | SQL Injection | 5.70% |
1. Stored Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is an attack whereby scripts, known as client-side scripts, are introduced by attackers that can affect the users visiting your applications. This unauthorised data can be leveraged to attack other users of your web application.
XSS attacks include accessing sensitive application data, logging user keystrokes or obtaining user passwords stored in the browser. When combined with other attacks, such as cross-site request forgery (CSRF), XSS can be used to perform privileged state-changing actions within the application, such as forcing a user to change their email address, potentially resulting in account compromise, denial of service or even information disclosure.
A stored XSS vulnerability is the most dangerous of the cross-site scripting vulnerabilities. Stored XSS is when a cyber criminal embeds a destructive script into a web app, which is then executed when a victim views the page. Social engineering techniques are then deployed by the hacker to get the victim to perform an action that will comprise the site even more such as clicking on a link or sending an email.
2. Broken Access Control
Improper access controls arise when an application’s security access is not fit for purpose. Failing to enforce restrictions can have devastating consequences. Access control issues can allow a malicious user to create highly privileged accounts, gain control of a user base and relay data.
Access control weaknesses are common due to the lack of automated detection and lack of effective functional testing by application developers. As it’s so difficult to automate the detection of these weaknesses, manual penetration testing is the best way to detect missing or ineffective access controls.
3. Vulnerable and Outdated Components
This might be the most basic vulnerability on this list and the easiest to avoid. Vulnerable and outdated components are a treasure trove for cyber criminals.
The use of unpatched, outdated, or vulnerable components in a web app compromises its security and opens it up to various cyber attacks. By analysing the application and associated framework components, an attacker is looking to understand where you might have weaknesses in your setup or vulnerabilities that can be exploited. Cyber criminals then tailor further attacks to see what they can find. To simplify their job, attackers focus on trying to find already written exploits for known component vulnerabilities, before trying to build new ones. Hackers are sophisticated and are always scanning the internet trying to find outdated software to exploit and monetise.
4. Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is a session riding vulnerability whereby a target user is tricked into executing unwanted commands via a web application in which they’re already authenticated. Browser requests include all cookies in CSRF attacks and because of this, if the user is authenticated to the site, it cannot determine the difference between real and forged requests.
The user can be tricked by the cyber criminal into sending a request via various means, either by phishing, social engineering or a malicious third-party website. It’s usually a state-changing operation, for example updating account credentials, sending private messages, submitting new passwords to override accounts or making a purchase unwittingly.
5. SQL Injection (SQLi)
SQL Injection (SQLi) is a web security vulnerability that has been around for years and is regularly at the top of the application vulnerability list. It allows an attacker to access the database by sending specially crafted SQL queries.
Following a successful injection, an attacker may have access to sensitive information, consumer data, passwords, billing information, credit/debit cards, API keys, etc. In some situations, a cyber criminal may be able to further exploit the database to escalate the attack and compromise entire servers, the backend infrastructure, or even conduct a denial of service (DoS) attack. Once access to this data is achieved, an attacker can then choose to steal, delete or modify that data.
How to prevent the exploitation of these web application vulnerabilities
Regular penetration testing is the primary way you can safeguard your organisation. Resilient cyber security relies on regular testing to check your security perimeters and the status of your components. At Bulletproof, our CREST certified penetration testers are experts in web applications and are there to advise you every step of the way.
We know how to bulletproof an organisation and provide a detailed report after each application penetration test so you can see what you’re doing well and where you need to implement critical remediation.
Defending against potential threats to your organisation's cyber security could be the difference between maintaining a safe and secure working environment or facing ongoing threats which compromise the sensitive and critical data of your entire workforce. Prevention is critical. Penetration testing could save you time, money and your reputation.
Find out more from our dedicated team of experts
Learn moreRelated resources
Trusted cyber security & compliance services from a certified provider
Get a quote today
If you are interested in our services, get a free, no obligation quote today by filling out the form below.








