What is the cyber kill chain?
What is the cyber kill chain and why is it important?
The cyber kill chain illustrates the structure of a successful cyber attack. It is effectively the hacker’s process from beginning to end, from scoping a target (reconnaissance) all the way to achieving their objective, whether that’s data theft or dropping and executing malware.
When approaching your cyber security strategy, you should align your defences to the cyber kill chain. Like Batman becoming fear, to defeat the hacker, you must become a hacker. As we talk about it a lot at Bulletproof, we felt it was about time we gave a thorough explanation of what it really is.
It's not enough just to spot a potential threat, you'll need to know what stage this potential threat is at to be able to correctly assess the danger. When sensitive data is potentially up for grabs, you need to know if it's time to panic or not. So, without further ado, let's discuss each step of the kill chain and what you expect to see.
How does the cyber kill chain work
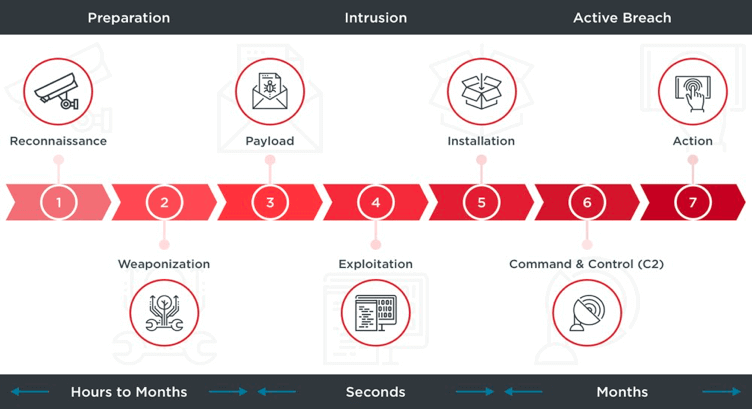
The cyber kill chain model outlines several stages of an attack, from reconnaissance to exfiltration, to enable organisations to plan, to detect and prevent sophisticated cyber attacks. There are 7 stages to the cyber kill chain: reconnaissance, weaponisation, payload, exploitation, installation, command and control, and execution. Businesses should be taking steps to prevent threats escalating in the earliest stage of the cyber kill chain to minimise the risk of an attack.
Stage One: Reconnaissance
The first step in the kill chain is reconnaissance. This can involve a variety of different things, the most common of which is scanning. Lots and lots of scanning. The majority of this is automated and you’ll find there are a vast number of scanning bots crawling the digital realms in search of fresh prey to ogle. Anything exposed to the internet will be subject to merciless scanning, the purpose of which is to uncover any known vulnerabilities, misconfigurations or outdated bits of software.
You’ll be surprised how quick these scanners are to descend on an asset. We were feeling delightfully devilish one morning at Bulletproof and set up a poorly configured sever hosting a simple web page that said ‘Hackers, do your worst!’ (or rather it said something along those lines with ruder words). By some time later that same morning we had over 11,000 log files, the majority of which involved scanning activity.
Just look at this spike of scanning activity below. A steady trickle shoots up to a veritable spike:
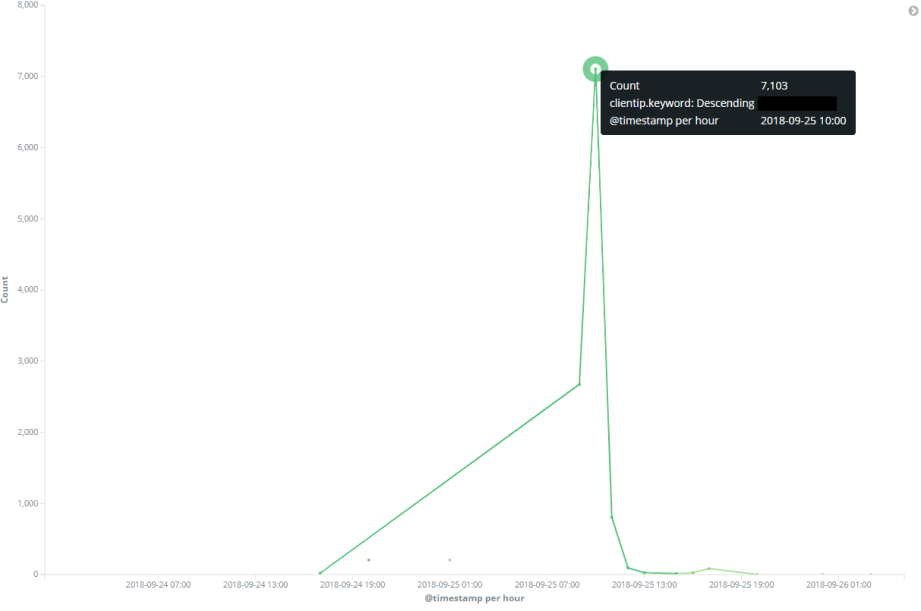
However, there are other aspects to reconnaissance, such as a simple Google of the business. There’s a lot a hacker can learn from online sources, such as extra domains associated with the business, office locations, staff names and email addresses (can be used in phishing or brute forcing), staff ID designs (from pictures) and more. The first step can be the most important. If you can detect or prepare for this type of activity, your cyber defences will be stronger for it.
A good place to start would be to get regular penetration tests. Seeing as these scans tend to be looking out for weaknesses or vulnerabilities, it’s probably best you find them first. Then, you can patch them up and sleep easy at night.
Stage Two: Weaponisation
The second step in the cyber kill chain is weaponisation, which is as ominous as it sounds. Once hackers have gathered as much information as they can and worked out your vulnerabilities, they’re going to go away and delve into their digital armoury and ready themselves for an assault. This is where they’ll craft a phishing email, select or create the right malware before thinking of the best approach of getting it into your network. Think of it like a scene from the A-Team where they go into a garage to do up their van for some outrageous chase/shootout.
It’s important to note that, at this stage, the attacker doesn’t actually interact with their intended victim. When it comes to mapping a defensive strategy against the cyber kill chain, unless the attacker is running some tests, there’s unlikely to be any logs or signs of ‘weaponisation’.

Stage Three: Payload
This is where things really start to get serious. The payload (sometimes referred to as delivery) is, as the name suggests, where the hacker drops the payload. This is the first stage that you could consider your network ‘breached’. This could be in the form of a phishing email with a malicious attachment, a contaminated USB device, or maybe a compromised user account. It could even be hackers exploiting a particularly severe vulnerability or misconfiguration that allows them to drop malware packages without having to do any of these.
What’s often easiest is to target users, either through standard phishing or the more targeted spear phishing. Spear phishing operates under the same principle as regular phishing, in which an email is sent with a malicious link or attachment in the hope an unsuspecting user will click or open it. Only in this case, a specific user is targeted and the email is highly tailored, usually containing enough relevant information to make it look genuine. It can also make use of a compromised email account or email spoofing to make it appear as if the email is coming from a trusted sender, giving it further credibility. Once the payload has breached your perimeter, the hard work is done. All the hacker has to do is wait.


Unless of course you have the right monitoring in place. If you do, then at this stage you can spot malicious emails coming in and have the sender blocked, and you can check the file extension of any attachment. Depending on the rules set up within your organisation, if this seems suspicious, this can be raised and investigated. In terms of compromised accounts, you can check the login times and, theoretically, their location for anything that deviates from the norm.
If you have file integrity monitoring (FIM) in place, changes to folders and files can be flagged and investigated. In this case, dropped malware can be isolated and swiftly removed. FIM is a high-value cyber defence, but one that can be difficult to implement and does pose the risk of getting flooded with alerts leading to alert fatigue. It requires quite a lot of knowledge to configure correctly.
Stage Four: Exploitation
The fourth stage of the cyber kill chain is exploitation and it’s where weaknesses within your system are exploited. Hackers can now start attempting to escalate privileges, make modifications or start dropping extra components.
If your SIEM monitoring services are tuned correctly, they should likely be going nuts at this point. With all sorts of happenings occurring within your environment, there should be enough log activity to let you know something’s not quite right. If you’ve got the right service from the right vendor configured in the right way, then you should also be able to stop the malicious activity in its tracks.

Stage Five: Installation
If the hacker has managed to get to this stage unimpeded, then you’re probably in trouble. As the name suggests, installation is the phase in which the malicious packages are actually installed. Often, such as in the case of ransomware, this can be instigated by a curious employee. Upon seeing a strange file on the system (a dropper), they might decide to run it just to see what it is before immediately regretting the decision as ransomware starts eating through every file it sees.
This can also happen earlier if the delivery method is a phishing email. All it takes is a member of staff to open that attachment and the hacker has a foothold. Whilst you can isolate a specific computer and take it offline to limit the damage, you have to be quick.
Mapping your defences against the cyber kill chain will hopefully mean attacks won’t get to this stage. But if the worst should happen, installations should definitely raise alerts, particularly if you weren’t expecting them. Spotting any activity such as this should allow you to act quickly to limit the damage. It’s also worth noting that offline backups are almost essential in these modern times. Ransomware can really cripple a business and even those who make the mistake of paying for their files to be decrypted often find they don’t get everything back as it was. If you’re correctly and regularly backing up, you can restore your shared network files back to a previous un-ransomwared point.
Stage Six: Command and Control
This is where the robots come in and assimilate you and all is lost. And that’s not as far-fetched as it sounds. Command and control or C2 is where the hacker has truly worked their way into your network and is establishing outbound communication to their own servers. It’s at this stage where an attacker has inserted their management and communication code into your environment. From here they can move deeper into your network, exfiltrate more information or even start destroying data and, if they haven’t got anything else going on, maybe commit a spot of Denial of Service.
Threat hunting has been something of a buzzword in the industry these days. Given that it’s a key feature of Bulletproof’s managed SIEM service, I myself have used the phrase "proactive threat hunting" no less than a thousand times. Threat hunting is where a trained analyst looks into logs and uses their expertise and knowledge to spot any suspicious activity that machines and correlations alone might fail to pick up on. When it comes to command and control activity, threat hunting is key. Spotting outbound communications beyond the norm often requires human input and knowledge of your environment.
Managed SIEM with analysts conducting this kind of threat hunting could protect you from the worst when it comes to hacking. This kind of defensive technology can be easily aligned to the cyber kill chain to keep your digital assets safe from external attack.
Stage Seven: Lights, Camera... ACTION
The final stage of the cyber kill chain is action, wherein hackers achieve their objective. This could be the planting and execution of malware, data exfiltration, inserting a backdoor, DDoS or whatever else they set out to do. It depends what the motivation of the hack is. State-sponsored attacks may include military or informational gain. Other attacks may intend to monetise stolen data or leak sensitive data. Some may be hacking for the sheer hell of it and simply be looking to deface an application or just see what they can find. The cyber landscape is a varied one, populated by all sorts.
Once again, even at this stage, a trained security team can limit the damage and resolve things as swiftly as possible, responding to events in the most appropriate way. As we have seen in the British Airways breach, in which hackers had access to data for over two weeks, and Citrix, where hackers had access to their internal network for six months, one of the biggest challenges businesses face from a cyber security perspective is one of dwell time. The time taken to detect a breach is often woeful. Sometimes it takes months for a business to even realise anything is amiss. Or, in the case of Marriott, years.
It’s clear that any defences in place in these instances didn’t take the kill chain into account at all, as evidenced by the fact that hackers went through every stage unhindered. Even after action, nothing was done for extended periods of time. If their defences were mapped against the kill chain, it’d be close to impossible not to notice some form of suspicious activity.
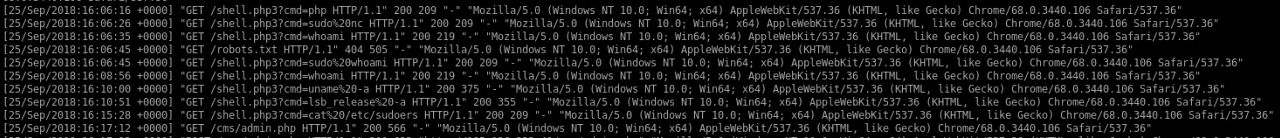
For example, returning to our hacker baiting server, hackers swiftly bit. They ended up uploading a web shell and used this to obtain usernames (a number of random ones we had made up obviously). They then checked the permissions of said usernames and would have used one of these to exfiltrate all our delicious data. That would have been their action had we actually put any data on the server, delicious or otherwise.
External and internal threats
Using the cyber kill chain to remain vigilant for threats isn’t necessarily reserved for the external attacks. As we have stressed over and over, internal threats are just as likely to compromise your business. Maliciously intended or otherwise, your own employees can cause a data breach or work malware into your environment far more easily than a hacker.
Being aware of the kill chain can help you defend against internal dangers. We’ve already discussed how you can spot reconnaissance activity and mysterious logins suggesting compromised accounts. When it comes to searching for insider threats, you have to skip right to exploitation. This can be noting accounts accessing areas not usually associated with their role such as secure areas, or it can be looking for installation attempts or file changes beyond the norm.
Prevention is obviously better than cure, so it’s good practice to make sure the right access controls are in place, restricting access to only what is necessary. Add the right monitoring to this and you can make sure that no one is trying to escalate their privileges, or that certain accounts haven’t been compromised or worse, make sure your staff aren’t deliberately abusing their access. This is of course easier said than done and relies on analysts with knowledge of your business to spot and investigate anything beyond the norm.

Go forth and beat the hackers
Now we’ve taught you how the hackers operate and how you can think like them to defeat them, it’s time for you to go out and choose your security solution. Speaking of which, let me tell you about managed siem. Our managed SIEM service puts skilled and experienced analysts behind the latest tech. Combining traditional log monitoring with machine learning and proactive threat hunting, we offer a 24/7 security solution that is – as you may have guessed – mapped to the kill chain. We think creatively and use the methods of a hacker to stop them before they cause any damage. Businesses of all sizes can benefit from this service, particularly as we have access to a wide range of threat data. managed SIEM is next generation threat protection and it’s aligned to the cyber kill chain.
Keep hackers out of your business
Find your vulnerabilities before a hacker exploits them. Discover penetration testing today.
Discover pen testingRelated resources
Trusted cyber security & compliance services from a certified provider
Get a quote today
If you are interested in our services, get a free, no obligation quote today by filling out the form below.









