Everything was easy to understand on a technical level and it was clear what the priorities were, which helped us remediate quickly and effectively.
Matt Boddy, Traced
Why choose Bulletproof penetration testing?
Continuous Security Protection
Protect your business 24/7 with automated scans included with every penetration test
Competitive Pen Test Prices
Bulletproof prices are highly competitive without sacrificing quality, keeping you protected
CREST Certified Security Experts
Pen test teams are qualified by industry recognised certification bodies, including CREST
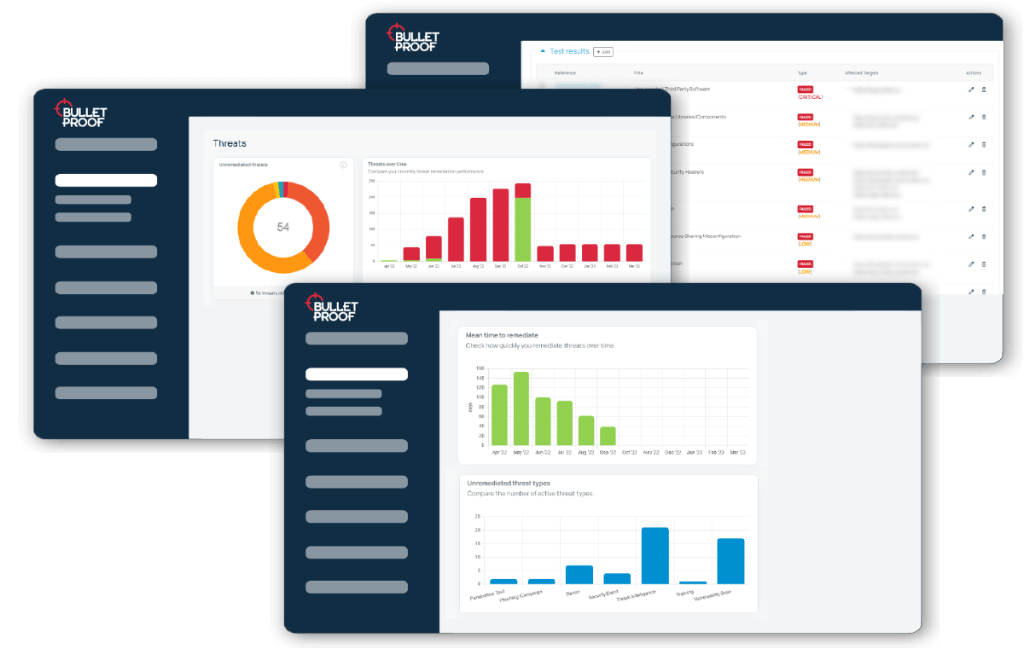
Modern Dashboard Driven Platform
Our simple to use dashboard prioritises test results and gives you key remediation guidance

A trusted team of certified penetration testers
Bulletproof takes pride in building and nurturing the best cyber talent to ensure our penetration testing services always get the best security outcomes. Our global teams of OSCP & CREST penetration testers highly skilled, speak at security events and have discovered CVEs.
Their years of experience delivering expert penetration tests for all types of engagement: network, infrastructure, web app, API, mobile app, cloud, and more. When you need a penetration test to deliver a trusted security assessment, you can rely on us.
Get a fast quoteTypes of penetration testing
Web App Pen Test
Internal and external network & infrastructure assessments give you complete visibility over your security weaknesses.
- Check services, patch levels and configurations
- Multiple test types, including external and internal testing
- Follows PTES best practice methodology
Cloud Pen Test
We test apps built for iOS, Android and other platforms to ensure security and safety across multiple devices.
- Proven expertise in iOS, Android & more
- SAST and source code reviews
- Uncover insecure functionality
Network Pen Test
Bulletproof pen tests comprehensively assess the security of authenticated & unauthenticated web apps, and APIs.
- Identify all security risks, including OWASP Top 10
- Authenticated, unauthenticated & API testing
- Includes DAST methodology and SDLC integration
Mobile App Pen Test
We assess the security of cloud infrastructure & applications from all major vendors including AWS, GCP, Microsoft 365, Azure, Dropbox & more.
- Includes AWS, Azure, GCP & more
- All cloud technology tested, including IaaS & PaaS
- Includes configuration reviews and 365 testing
Penetration testing methodology
-
Scope definition & pre-engagement interactions
Based on your defined goals, we’ll work with you to develop a tailored testing strategy.
-
Intelligence gathering & threat modelling
In this reconnaissance stage, our experts use the latest groundbreaking techniques to gather as much security information as possible.
-
Vulnerability analysis
Using the latest tools and sector knowledge, we’ll uncover what’s making your critical assets vulnerable and at risk from attack.
-
Exploitation
Using a range of custom-made exploits and existing software, our penetration testers will test all core infrastructure and components without disrupting your business.
-
Post-exploitation
The team will determine the risks and pivot to other systems and networks if within the scope of the test. All compromised systems will be thoroughly cleaned of any scripts.
-
Reporting
Our security team will produce a comprehensive report with their findings. You’ll have the opportunity to ask questions and request further information on key aspects of your test.
-
Continuous Security
New threats are discovered every day, so Bulletproof includes automated security scans to help you keep on top of new security weaknesses.
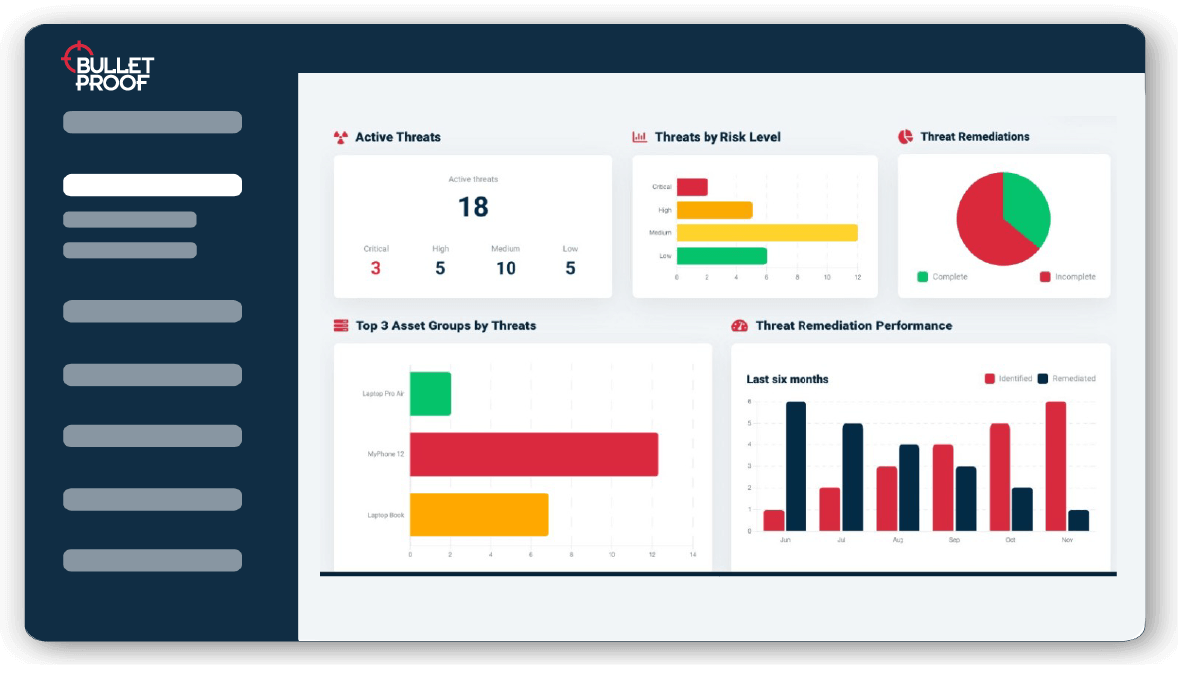
Penetration testing to boost security & meet compliance
Prevent data breaches and cyber attacks with CREST-certified penetration tests from Bulletproof. Our expert pen testers can test web and mobile apps, cloud, networks and other infrastructure. With 7+ years in the industry, our penetration testing services have a proven track record of helping businesses stay ahead of the hackers and meeting compliance.
-
Uncover your security weaknesses
Penetration testing uses human skill & insight to uncover threats
-
Automated security scans
Continuously uncover the latest security threats to your business
-
At-a-glance prioritisation
Results delivered in an modern dashboard-driven platform
-
Key remediation advice
Fix issues fast with remediation advice included with each threat
-
Support sales growth
Give customer confidence that you take their security seriously
-
Helps with compliance
Meet ISO 27001, PCI DSS, GDPR, SOC2 requirements & more
Get a fast penetration test quote
One of our expert pen test consultants will get back to you as soon as possible.